Reddit上发布的一段视频展示了一个远程端口漏洞,该漏洞在《太初时代》(ancient age)中使用
2019-09-27
426
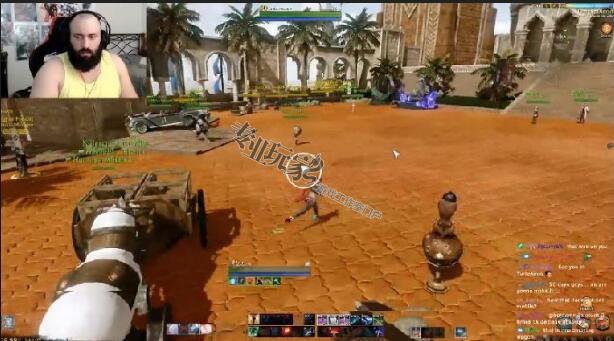
Reddit上发布的一段视频展示了一个远程端口漏洞,该漏洞在《太初时代》(ancient age)中使用,通过驾驶一辆汽车跟踪一名主播,从而诱骗他。
一位评论者解释了到底发生了什么,
“TLDR版本
这是昨天直播时发生的。有人利用该漏洞用车辆传送/跟踪拖拽拖拽拖拽拖拽拖拽拖拽。他们试图把用户拖到车里,要么把他们从1000米高处传送下去,要么把他们送到水下,把他们从上面传送过来淹死。”
较长的版本更详细地描述了这种利用的机制,
“长版
Merv Lee Kwai (@khrolan)曾说过,如果有人可以在直播服务器的流媒体中公然使用第三方软件和客户端修改,并且第二天仍然不被禁止,那么我们很难相信他的话。
我们先来确认一下视频中的两个人。流光是一个逃跑,并试图避免被“推入”浮动的车辆。剥削者是开车的人。
车辆继续传送到拖缆坐标的方式似乎是脚本化的,而不是手动控制的。这种传送到空中或水下的方式似乎是硬编码的,但一旦目标进入车内,就会手动触发。
似乎这个漏洞已经存在,并自alpha版以来被报道过,这里是关于这个主题的许多线程和视频之一。这个线是5年前的,这个视频是4年前的。
传送黑客上交交易包
https://www.youtube.com/watch?v=7f0FCRVnpk8
Merv Lee Kwai应该采取措施在9/27直播期间解决这个问题,然后概述如何在发布前解决。如果在10月15日发布之前还没有修复,那么很有可能出现这样的情况。
假设你最终通过了30分钟的排队,并在游戏中玩了几个小时。然后,由于该漏洞的广泛使用,服务器将回滚。在这一点上,你不仅失去了所有的进步,而且更糟的是,你又回到了队列中。我们不要忘记,服务器很可能会被撤下补丁,这可能会持续数周,甚至数月。”
专业玩家网游戏工作室信息交流平台,为游戏工作室提供最全面的游戏工作室项目,游戏加速器,游戏防封IP,集游戏供求信息交流为一体的游戏工作室门户网站。
原文:
A video posted to Reddit showcases a teleport exploit used in ArcheAge to troll a streamer by following him with a vehicle.
A commenter explains exactly what’s happening,
“TLDR Version
This happened during a live stream yesterday. Someone trolled the streamer by using the exploit to teleport/follow the streamer with a vehicle. They attempted to scoop the user into the vehicle then either: teleport drop them from 1000 meters above, or teleport them underwater to drown them by teleporting the vehicle above them.”
The longer version goes into much greater details on the mechanics of this exploit,
“Long Version
It's hard to take Merv Lee Kwai's (@khrolan) statement that they will take third-party software and client modification seriously when someone can blatantly use them during a stream on the live servers, and still go unbanned the next day.
Let's first identify the two individuals in the video. The streamer is the one running away and is trying to avoid getting "nudged" into the floating vehicle. The exploiter is the one driving the vehicle.
The way the vehicle continued to teleport to the coordinates of the streamer appears to be scripted and not manually controlled. The way the vehicle teleported high into the air or under water does appear to be hard-coded, but triggered manually once the target is inside the vehicle.
It appears this exploit has existed and been reported since alpha, and here's one of many threads and videos on the topic. The thread is from 5 years ago, and the video is from four years ago.
Teleport Hackers Handing in Trade Packs
https://www.youtube.com/watch?v=7f0FCRVnpk8
Merv Lee Kwai should take steps to address this during the 9/27 live stream, then outline how it will be resolved before launch. Here's a likely scenario if this isn't patched by launch (October 15).
Let's say you finally got past the thirty minute queue and managed to play a few hours in-game. Then comes the announcement of a server rollback due to widespread use of the exploit. Not only do you loose all progress up to this point, but to add insult to injury, you are placed back into queue. Let's not forget that the servers would likely be taken down to patch, which could stretch for weeks if not months.”
免责声明:部分内容转自其他媒体,转载目的在于为游戏工作室传递更多信息,如因作品内容、版权和其他问题请 联系客服